Network Architecture of Treason
(12/24/05)
So how would an agency go about surveillance on overseas Internet traffic on a massive scale?
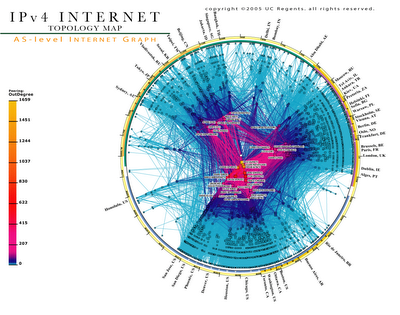
First of all, one has to place monitors, probes or taps on the Internet. Where would one place them? That's pretty simple. Let's look at CAIDA's Internet topology map. http://www.caida.org/analysis/topology/as_core_network/AS_Network.xml
This shows a snapshot of the major "choke" points for Internet traffic as it exists today. There are not that many core points, especially if we are only concerned with international traffic.
(Post Post - Does this image look familiar??)
Let's just say that we want to set up monitoring on the top 20 nodes in this diagram. Now what does our monitor or probe need to look like in terms of compute power and storage.
For that we can go to a typical packet trace analysis of one the core carriers at this link.
http://ipmon.sprint.com/packstat/packet.php?040206
Notice anything interesting here? Link utilization for these links is minimal. These OC48 links can support up to 2.5 gigabits/sec but the utilization is barely more than 100 megabits per second. And the storage needed for these traces is minimal as well.
But do we have to monitor all that traffic? If we look at the application breakdown, we see that appr. 50% is http traffic. If we add email, the total is about 60%. That means that we're looking at doing deep packet inspection, etc. on only about 50 or 60 megabits/ sec. You can do that with an off-the-shelf $1000 Dell server. Storage is just as cheap. In fact, I found a little Powerpoint slide on the Internet that Amogh Dhamdhere from Georgia Tech did, illustrating the Sprint IPMON architecture.
http://www.cc.gatech.edu/classes/AY2004/cs8803ntm_fall/amogh.ppt
So how does one spot a DoS attack or worm? Simply by recognizing a pattern or signature in the traffic. What is the difference between a malicious pattern and a certain set of words in an email or an http flow? Simple semantics…or semiotics depending on your philosophy.




No comments:
Post a Comment